NIST Cybersecurity Framework
If you’re looking to land government contracts, the NIST Cybersecurity Framework can help you better protect data and win more deals.
Connect with a member of the R3 sales team today



NIST comes in many flavors, including NIST-CSF and the NIST Special Publications, such as NIST 800-53 and NIST 800-171.
Any organization, regardless of sector or size, can use the Cybersecurity Framework to better manage and reduce cybersecurity risks by customizing practices and determining activities that are important to critical service delivery.
How to implement NIST Cybersecurity Framework
After familiarizing yourself with the framework, assess the current state of your organization before establishing a cross-functional team to own the process.
From there, you’ll want to identify and prioritize assets, perform a risk assessment, determine the desired target state for cybersecurity maturity based on the NIST framework, and develop a roadmap to get there. Next, implement security controls and measures and develop and implement an incident response plan.
Throughout this process, you’ll want to provide cybersecurity training to employees, implement continuous monitoring mechanisms, document all cybersecurity policies, procedures, and practices, and establish a reporting mechanism to communicate cybersecurity status, incidents, and improvements to all relevant stakeholders.

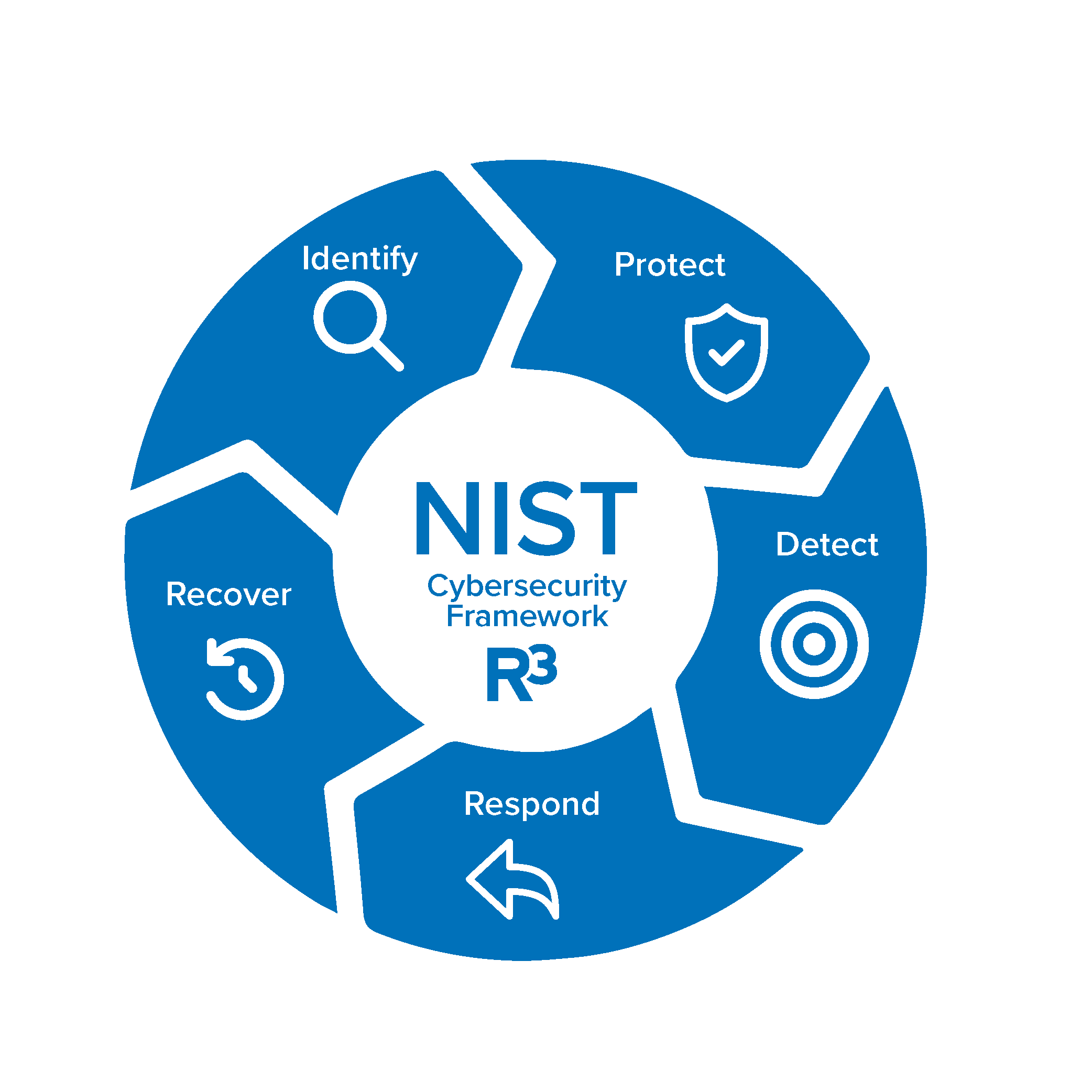
The Five Elements of the NIST Cybersecurity Framework
1
Identify
2
Protect
3
Detect
4
Respond
5
Recover
Benefits Of adopting the NIST Cybersecurity framework
The NIST Cybersecurity Framework provides a holistic and practical approach to cybersecurity risk management, helping organizations enhance their resilience to cyber threats & adapt to the ever-evolving cybersecurity landscape.
Additional benefits of the NIST Cybersecurity Framework include:
- An adaptable framework that can be tailored to the specific needs, priorities, and risk profiles of your individual organization.
- The establishment of a common language for communicating & managing cybersecurity-related activities across different departments & organizational levels.
- Enhanced visibility into your organization’s cybersecurity posture.
- Improved incident response.
- Better supply chain security.
- More efficient resource allocation.
- And more!


Download The Ultimate Guide to MSPs
Check out our free eBook The Ultimate Guide to Managed Service Providers (MSPs) today.
Trusted by 1000+ customers
“We went out to find a managed services provider, and with R3 it’s become more of a partnership. They have the best intentions for KDB and want KDB to succeed. It’s been more than we asked for when we started the process.”

“An outstanding example of the level of detail and clarity for all R3 projects. The team made incredible progress on this critical project and most importantly - they completed it on-time.”

“R3's ability to manage large and complex projects is easily a 10/10. And in regard to their experience and technical ability to keep our systems protected, we have been very satisfied. We see R3 as a partner and we trust them.”

“Whether doing business over the phone, via email, or in-person, it’s always the same, excellent customer service. As someone who has been in the customer service industry since the early 80’s, I appreciate when businesses own and recognize that their level of service will determine their success.”

“We have someone who we trust and believe in when we call with a problem. To call an have someone who just talks to us a like a person. R3 follows through with everything they say they're going to do.”

“The flexibility of the R3 team was integral to the success of this move. As unforeseen challenges popped up throughout the project our business faced no interruptions to daily operations thanks to the ingenuity and experience of the R3 team.”

FAQ
The NIST Cybersecurity Framework is governed by the National Institute of Standards and Technology, or NIST, a government-funded agency under the Department of Commerce. It’s the US Government’s take on data protection and cybersecurity best practices taken from other frameworks.
NIST is required of any organization that does business with the US government and many state agencies.
The NIST cybersecurity framework consists of three main components: the Framework Core, Implementation Tiers, and Profiles.
The Framework Core is a set of desired cybersecurity activities & outcomes. It consists of five concurrent and continuous Functions—Identify, Protect, Detect, Respond, and Recover—which provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk.
Tiers describe the degree to which a company’s cybersecurity risk management practices exhibit the characteristics defined in the Framework Core, from Partial (Tier 1) to Adaptive (Tier 4), or informal and reactive responses, to agile and risk-informed ones.
Profiles are a company’s unique alignment of their requirements & objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles can be used to identify opportunities for improving a company’s cybersecurity posture.
